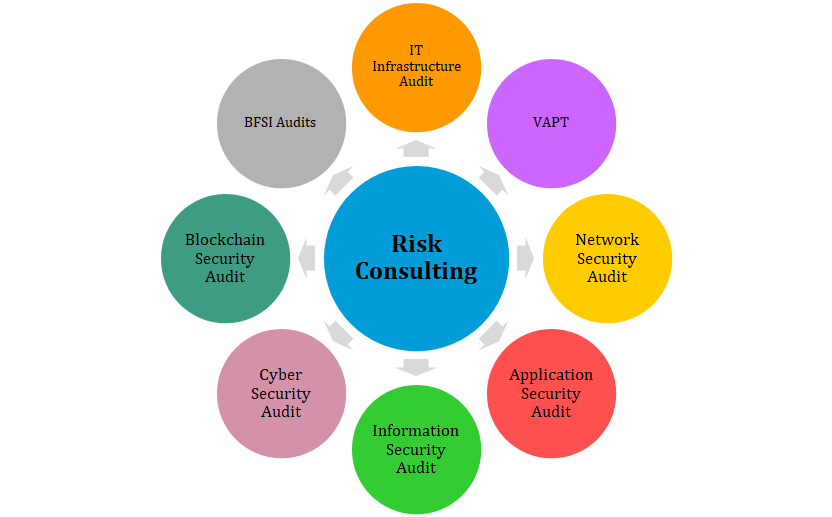
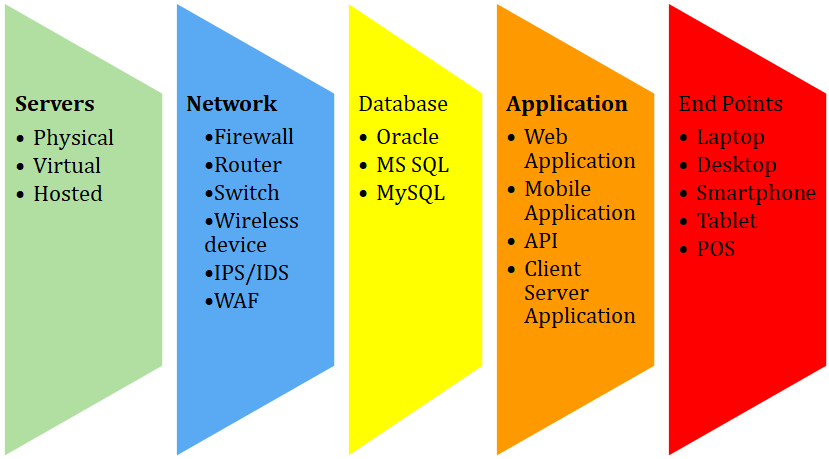
IT infrastructure audit is a comprehensive audit covering vulnerability assessment, penetration testing, secure configuration review, source code review of an organisation’s IT assets – Servers, network devices, databases, applications and end points.
Vulnerability assessment is the process of identifying and quantifying vulnerabilities or potential threats to each resource and mitigating or eliminating them.
Our Teams work closely with the client to identify the vulnerabilities and address them thus improving the organisation’s IT security posture.
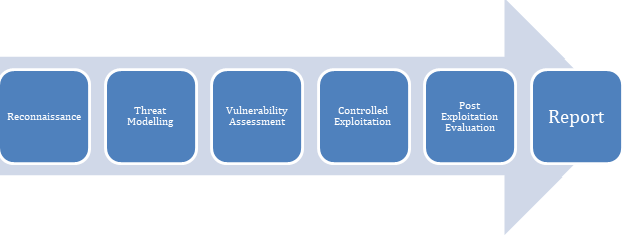
A penetration test is a method of evaluating the security of a computer system or network by simulating an attack similar to a malicious hacker. The process involves an active analysis of the system for any weaknesses, technical flaws or vulnerabilities.
This analysis is carried out from the position of a potential attacker, and can involve active exploitation of security vulnerabilities. Any security issues found would be presented to the system owner together with an assessment of their impact and often with a proposal for mitigation or a technical solution.
Network Security Audit primarily focuses on the logical, physical and environmental security of an organizations network and networking components.
As part of the network audit, we conduct a vulnerability assessment and penetration testing of the network components in line with the methodology mentioned above.
Network Performance audits focuses on understanding and highlighting performance bottlenecks due to network components.
Application Security audit focuses on conducting vulnerability assessment and penetration testing for exploitable vulnerabilities with the intention of exploiting vulnerabilities in
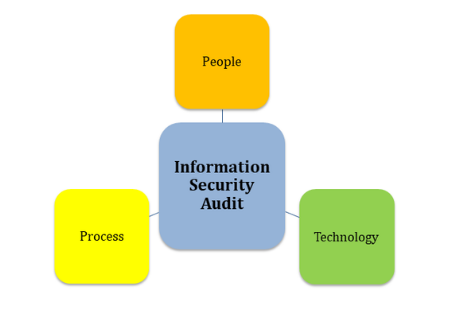
Information Security Audit is focussed on auditing an organisation’s security posture encompassing people, process and technology for the scope defined in the client engagement.
The audit is conducted in compliance with ISO27001 standard requirements.
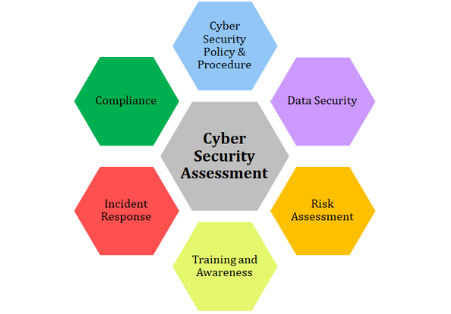
A cyber security assessment is a comprehensive cyber review of the organisation and its IT estate. It identifies the threats, vulnerabilities and risks the organisation faces, and the impact and likelihood of such risks materialising.
The assessments are conducted based on cyber security frameworks and covers areas depicted in figure 6
Imperium Solutions works extensively with the BFSI sector to conduct compliance audits against regulatory requirements defined by RBI, SEBI, UIDAI, IRDAI, etc. Some of the banking audits conducted by our team are
Imperium Solutions have the technical skill-set to design and implementation a secure IT infrastructure at a client organization.